
Guide on how to unlock the “Basement Burst Achievement” with information gathered during the Honeypot gig.
Summary
During the Honeypot gig, you get the hint “[Optional] Delve deeper for additional information”.
Harvesting “EL_1000E” leads you to “Arnold Jesse“, his Tweeter leads you to “InTheFlameWeGo” which gives you their server IP “30.76.93.43” and admin user “Master_Cocaine_XXX” by harvesting. Harvesting the admin gives you his MAC address “30:0A:0B:E5:00:B0” needed for NetStorm.
- Terminal “inject -s 30:0A:0B:E5:00:B0 -t NetStorm.exe“
- => to get the malware ready (“NetStorm_Injected_30:0A:.exe”)
- Terminal “use -x FTP_Bounce_Attack -version 1.0.0 -ip 30.76.93.43“
- => to connect to the server, select and upload your malware with Terminal “upload“
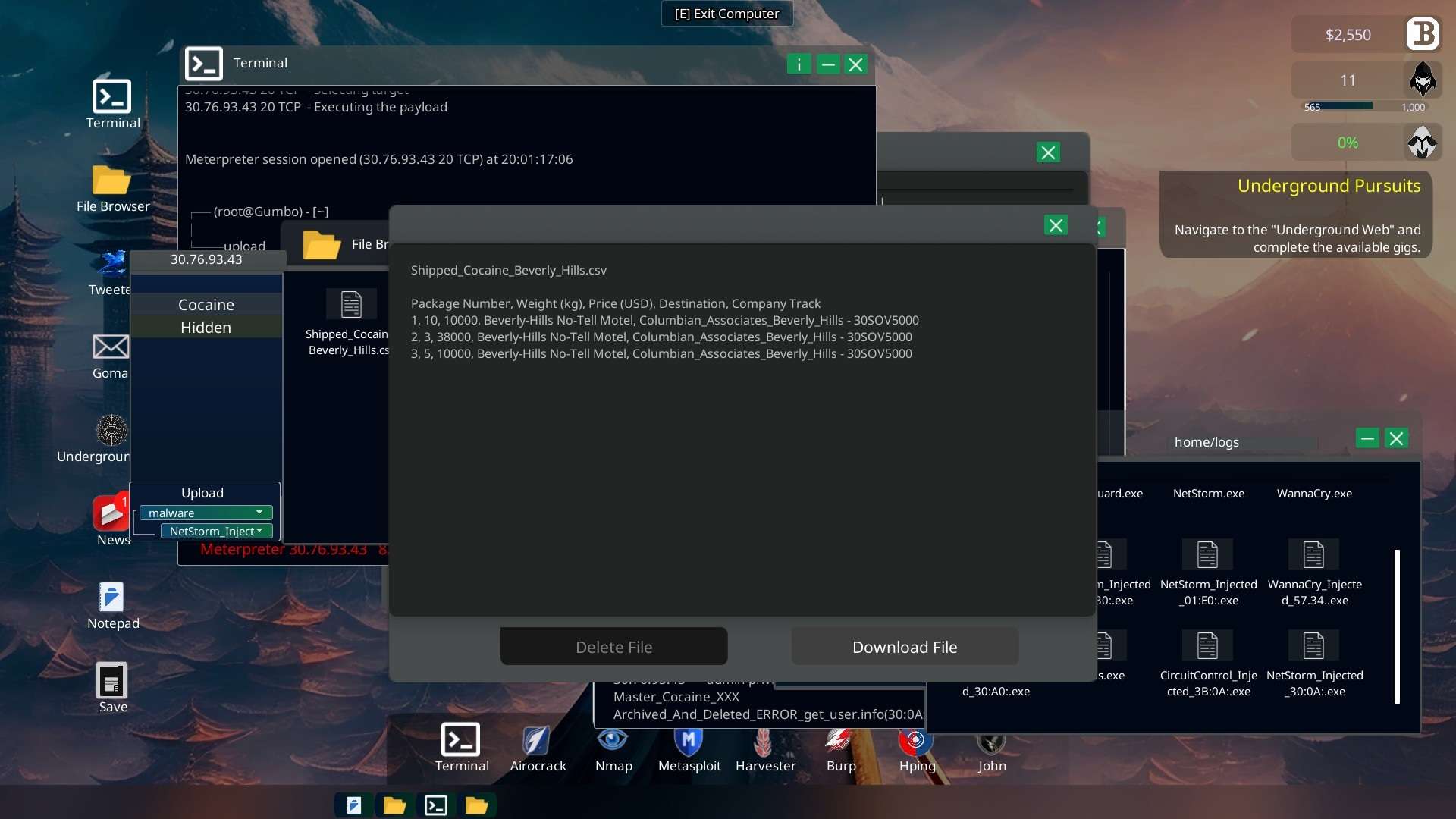
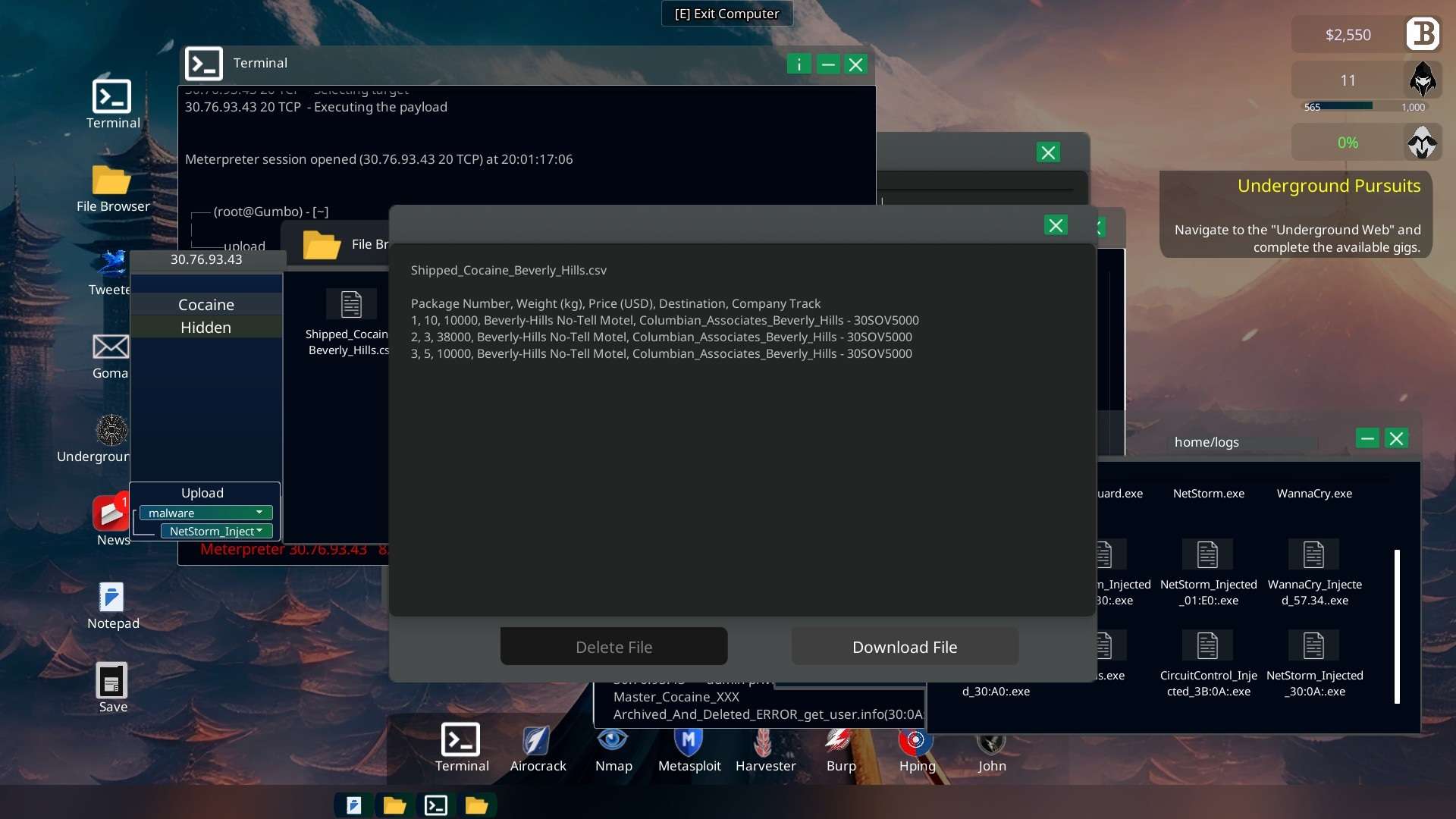
Download the hidden file “Shipped_Cocaine_Beverly_Hills.csv” and send it to the LAPD.
Terminal “send -f Shipped_Cocaine_Beverly_Hills.csv -h lapd.gov“
All Steps Detailed
During the Honeypot gig you get the hint “[Optional] Delve deeper for additional information”.
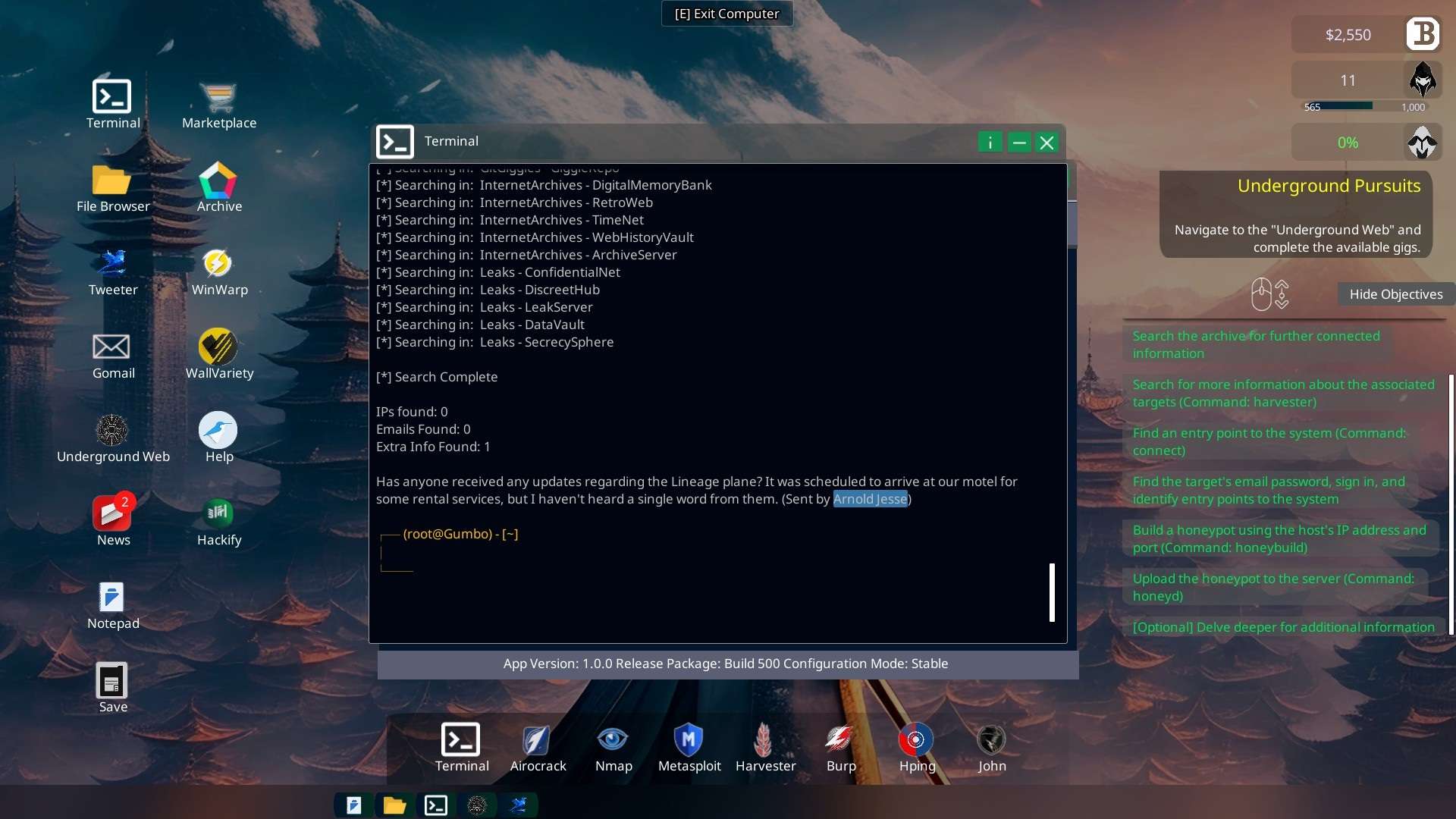
- When using the harvester on “EL_1000E” (the operation code for the plane) you stumble across the name “Arnold Jesse“
Terminal “harvester EL_1000E“
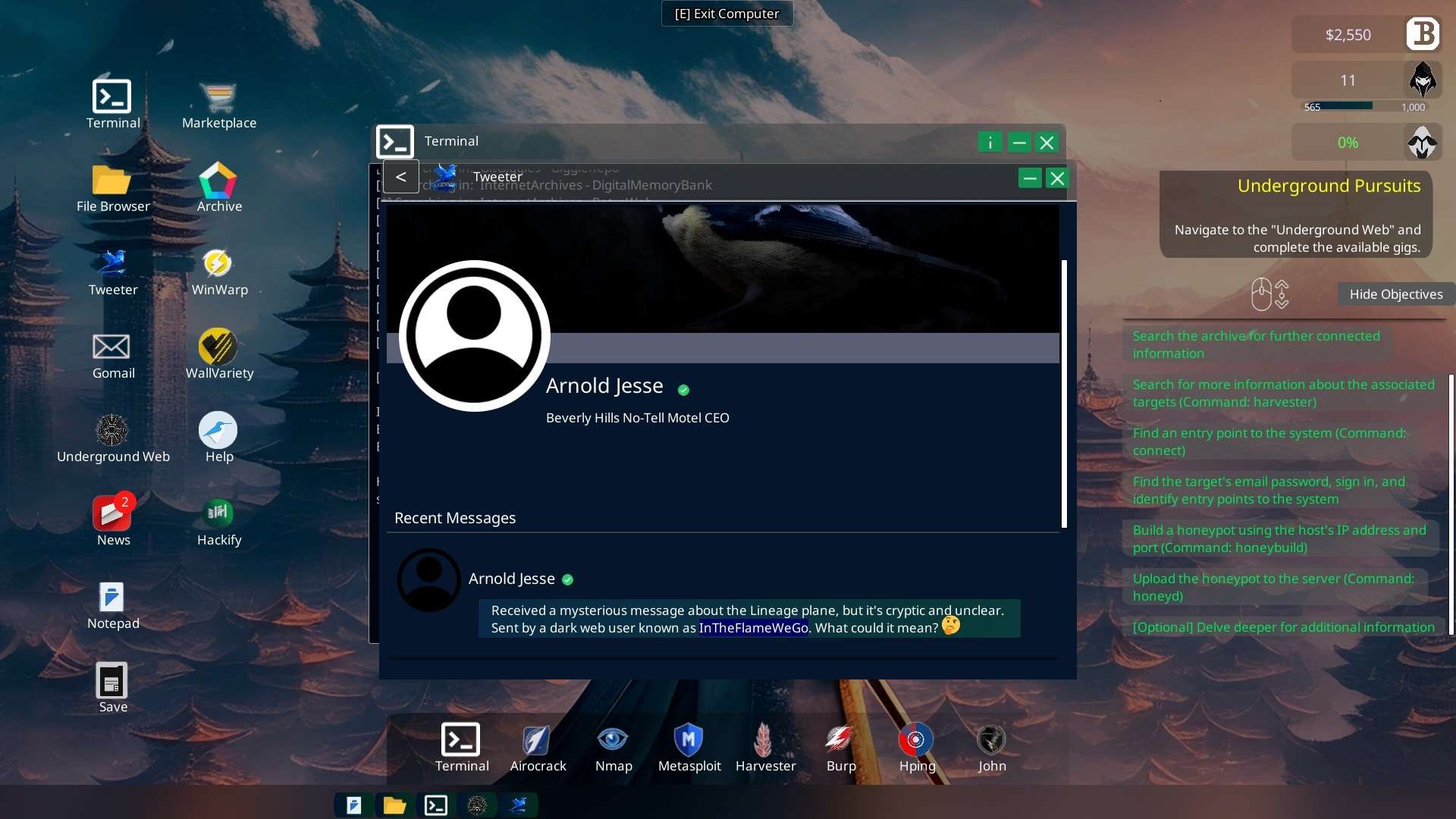
- On Arnold Jesse’s Tweeter account you learn about a user called “InTheFlameWeGo“
Tweeter App -> “Arnold Jesse”
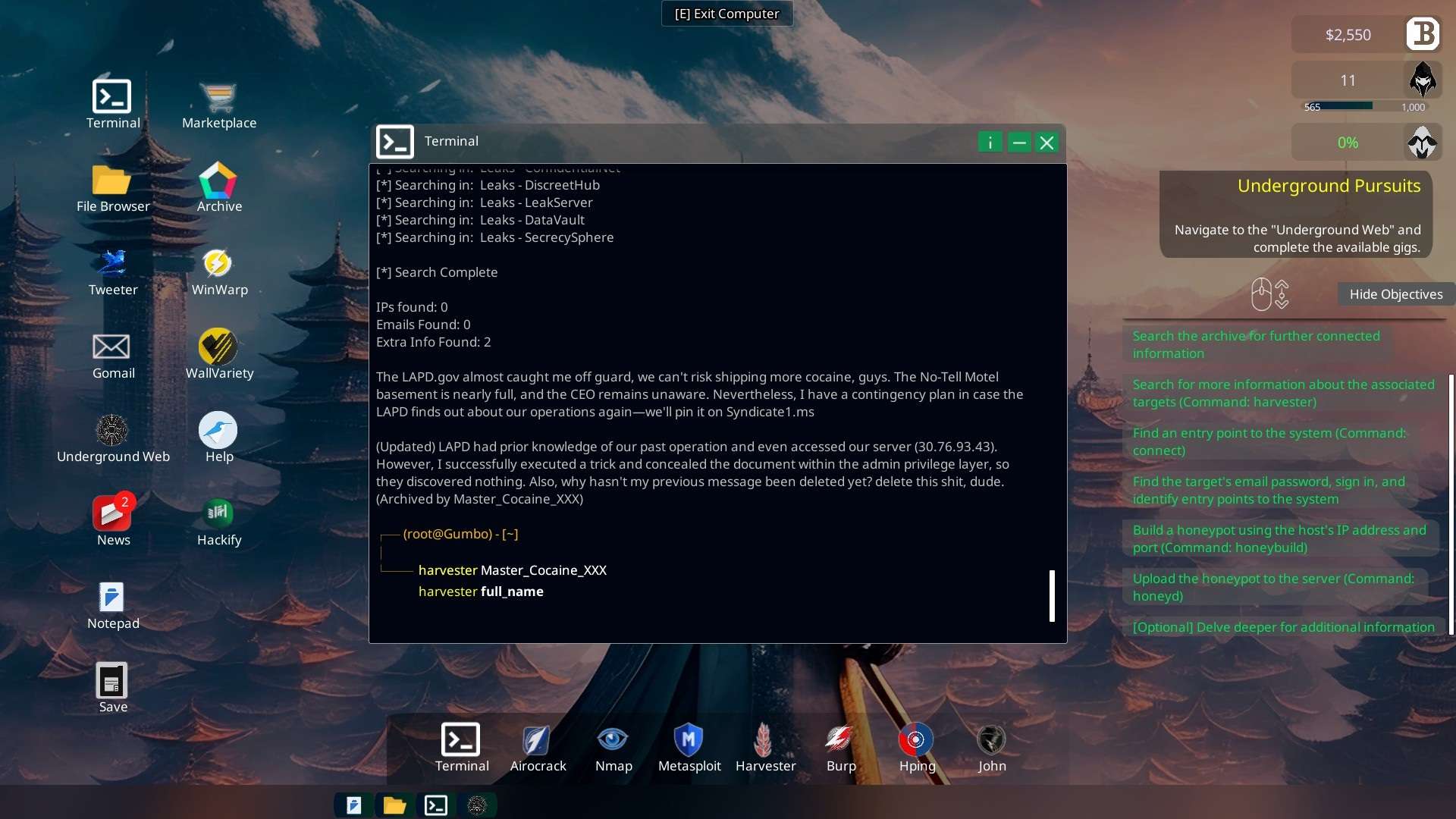
- When harvesting the user name “InTheFlameWeGo” you learn their server IP “30.76.93.43” and that an admin privilege elevation is required to access a hidden document. -> eg NetStrom will be needed.
- You also learn about the admin called “Master_Cocaine_XXX“
Terminal “harvesterInTheFlameWeGo“
- When harvesting the user name “Master_Cocaine_XXX” you get a MAC address “30:0A:0B:E5:00:B0“.
Terminal “harvesterMaster_Cocaine_XXX“
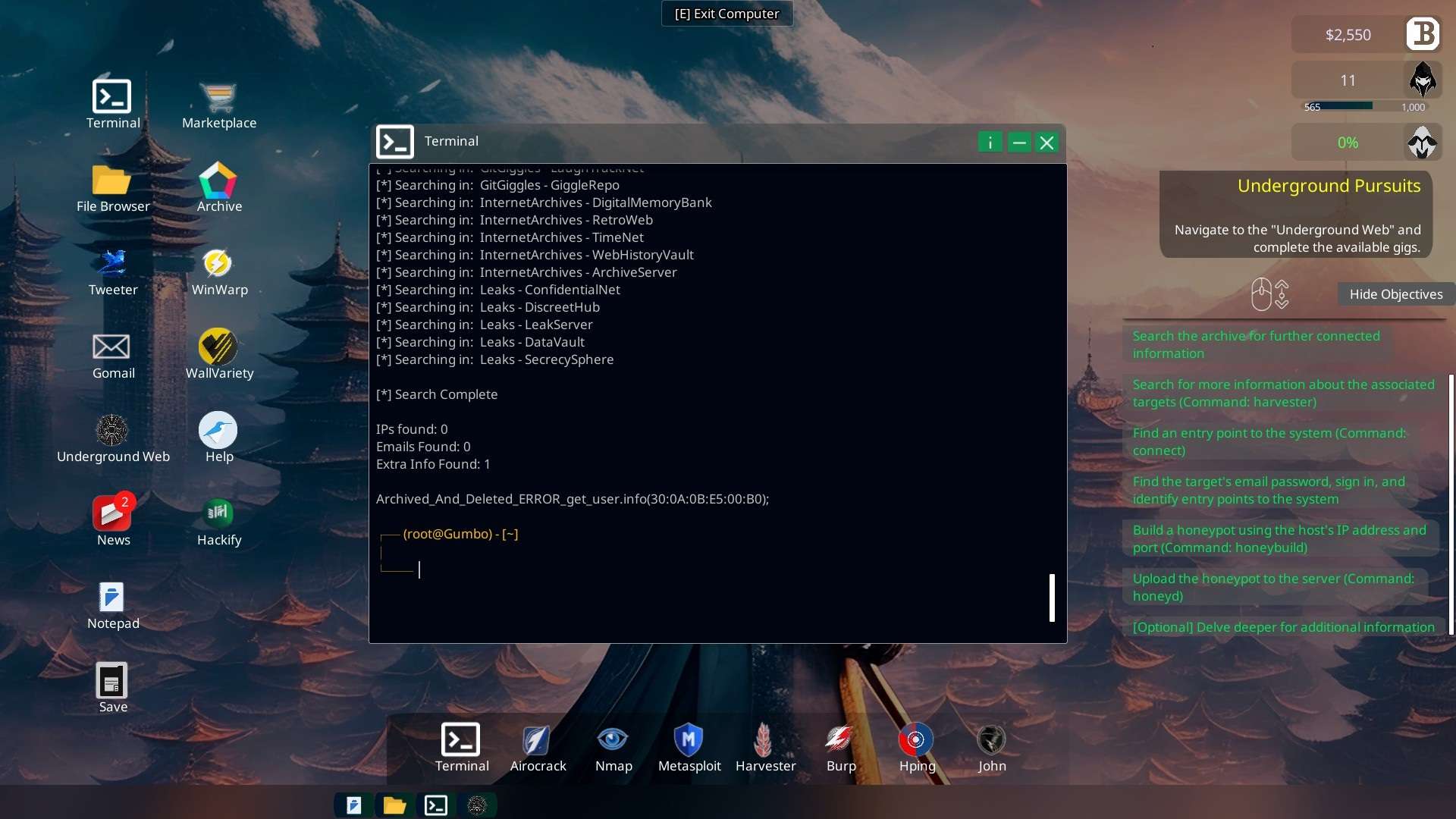
- Inject the MAC address into NetStorm.exe malware
Terminal “inject -s 30:0A:0B:E5:00:B0 -t NetStorm.exe“
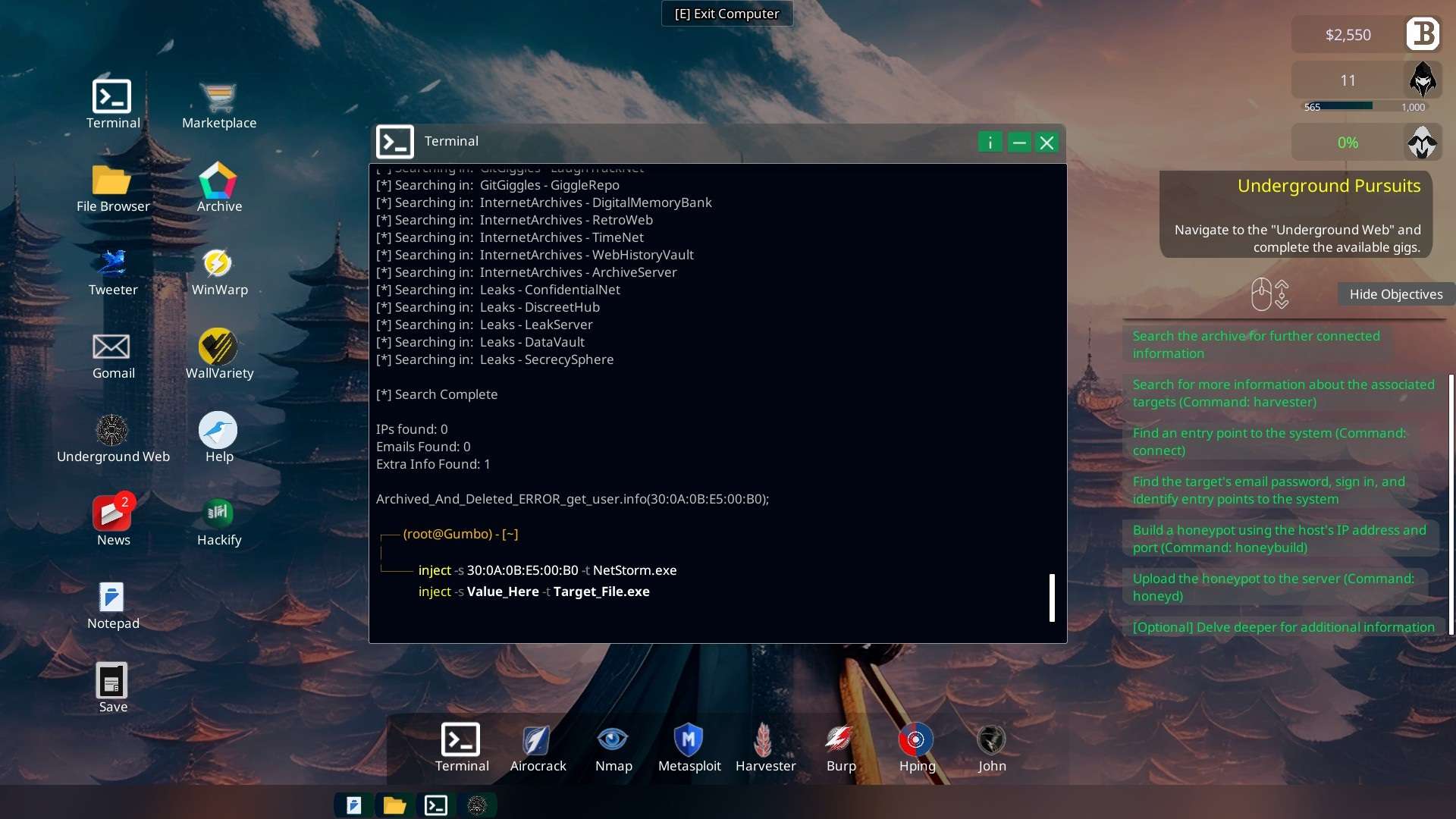
- Connect to the server IP 30.76.93.43 with “nmap” and “FTP_Bounce_Attack 1.0.0” commands.
Terminal “nmap 30.76.93.43“
Terminal “use -x FTP_Bounce_Attack -version 1.0.0 -ip 30.76.93.43“
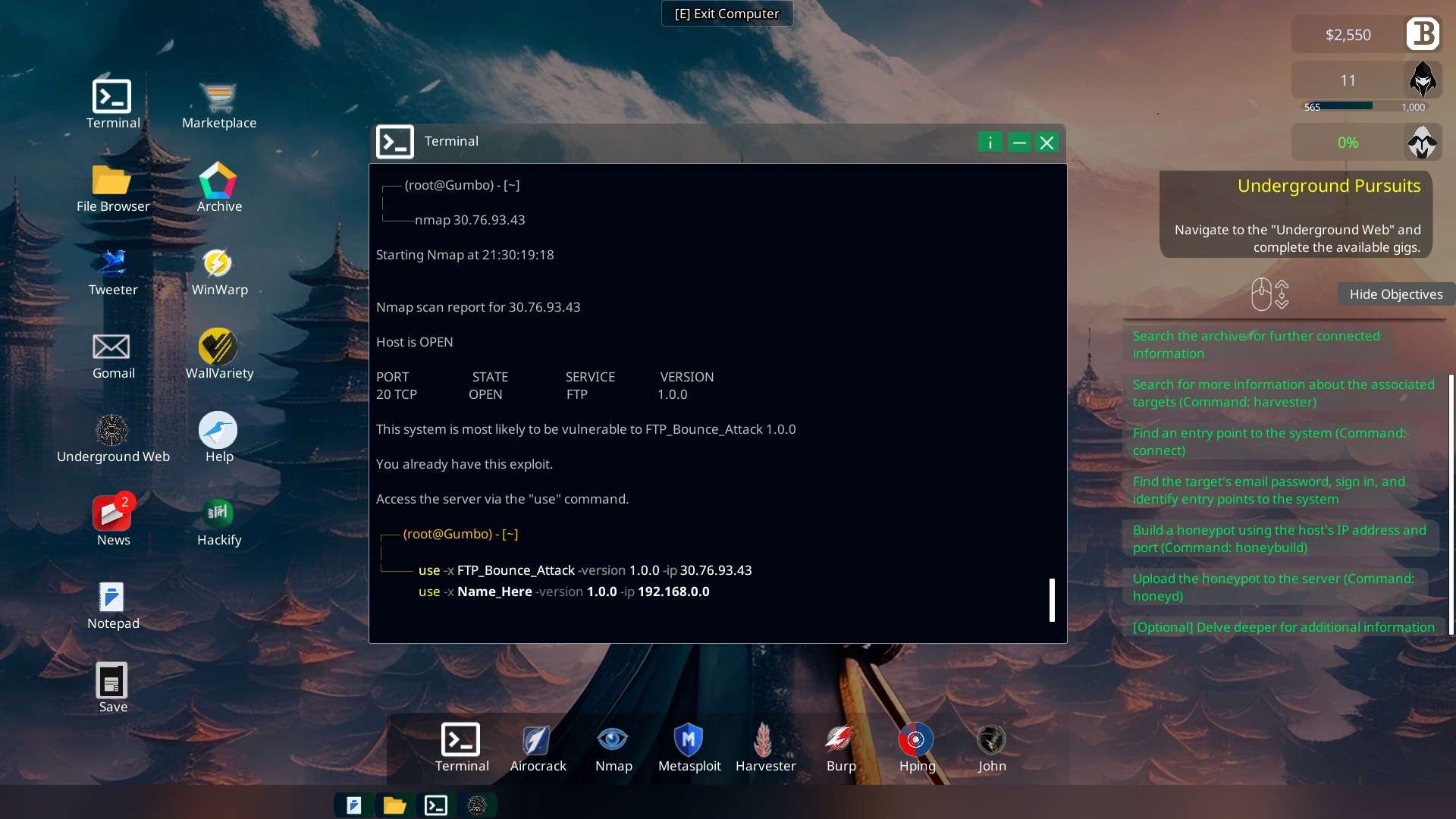
- Upload your malware “NetStorm_Injected_30:0A:.exe” to the server with command “upload”
On bottom left of file browser select malware/NetStorm_Injected_30:0A:.exe
Terminal “upload“
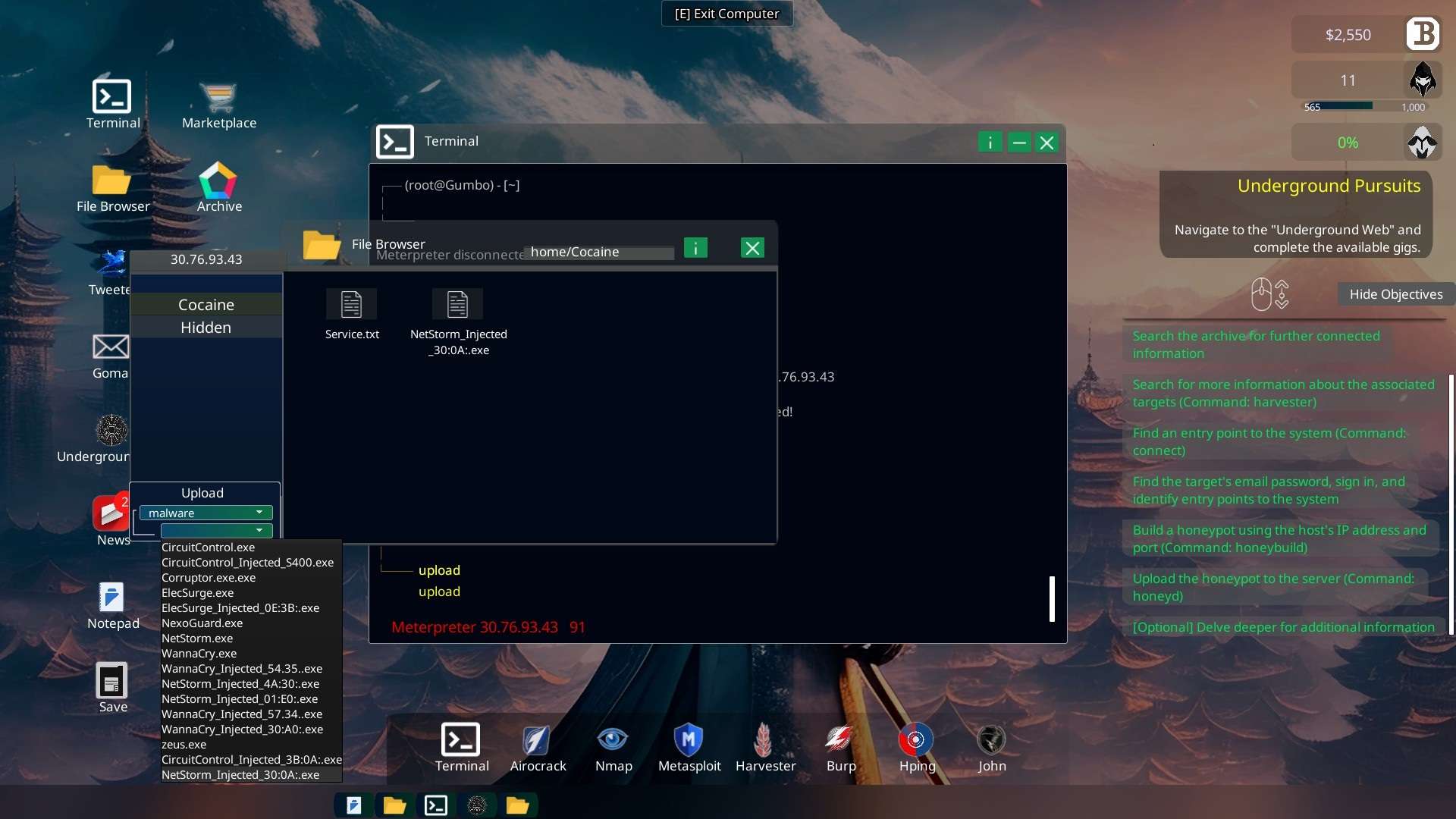
- The folder “Hidden” appears on the server and allows you to download file “Shipped_Cocaine_Beverly_Hills.csv”. Send it to the LAPD and you’re done.
Terminal “send -f Shipped_Cocaine_Beverly_Hills.csv -h lapd.gov“





Be the first to comment